Technology is a great invention that a human ever had in his life, but what happened when such a blessing turns into a curse for humankind. Yes, in this article, we will talk about new technology advancement dubbed Air gap computers, which remain isolated from unsecured networks like public wifi or unsecured LAN.
Air Gap System in Networking:
Air gap computers seem most secure than a normal PC system. Air gap system or computers are used in the area of military networks, payment networks where credit/debit card payment is processed, industrial control system works on critical infrastructure. All these systems are kept isolated means keep the local internal network away with the aim to prevent intruders to enter into corporate networks and thus saves sensitive data.
Recent breaches:
However, hackers have found a way to infiltrate the air gap system. With the advancing technology, it makes easy for hackers to gain access of such secured system without accessing it physically. An attack that involves the usage of USB drive can infect these isolated systems. Currently, Stuxnet malware had disrupted the uranium enrichment plant in Iran. Researchers in Israel also found that radio waves could breach air gap system, earlier the NSA (National Security Agency) has been involved in monitoring radio signal data to siphon data in China, Russia, and Iran. Even researchers at Ben-Gurion University lab discovered the technique dubbed “AirHopper” where radio signals are used to draw off the data from air gap systems.
AirHopper targets infected computers to siphon passwords and data using radio signals, which is generated from the computer’s video card. Then, such infected computer initiates and transfers, radio signals that are received by a mobile phone. FM radio receiver that is already built into mobile phones receives radio signals in the absence of cell network and the internet. Thus, an attacker can turn innocent device into a spying tool. Though company thinks that its air gap system is safe but a single mobile phone placed in the employee’s pocket can be a source of AirHopper attack.
How attacker breach Air gap system:
Three main Hurdles for an attacker to breach air gap system like compromising the network, sending commands, withdrawal of the data.
- The Attacker has to gain system by using insider or outsider for example, a consultant who has an authority to access the system and can use the infected USB device to contaminate the computer. Attackers can use chain attacks while the manufacturing or shipping of the unit.
- After gaining the access, attacker works on sending command and updates the malware over the internet that requires creativity in designing and updating the malware.
- The attacker causes damage to the system by exploring a way to draw off the stolen data from the air-gapped system.
Different Air Gap Attack patterns and Mitigation:
Symantec has gathered some attack patterns being carried out in an air-gapped system, which are discussed as under.
AirHopper:
As we discussed above, AirHopper is used to withdraw data through the FM signals being sent out from a computer’s graphic card. AirHopper applies the computer’s video display adapter to send FM-compatible radio signals to a device with an FM receiver. Attackers use a technique that could contaminate computers with malware by using USB devices, or by supply-chain tampering. To carry out this attack, the receiver needs to be in the radius of eight yards of the radio signals.
AirHopper Mitigation:
The AirHopper technique is quite possible in the real world because exposing Smartphone is within reach in cyber criminals. Smartphone should be restricted in certain premises of office. On the other hand, the use of electromagnetic defensive should be there to stop radio signal transition from the isolated network.
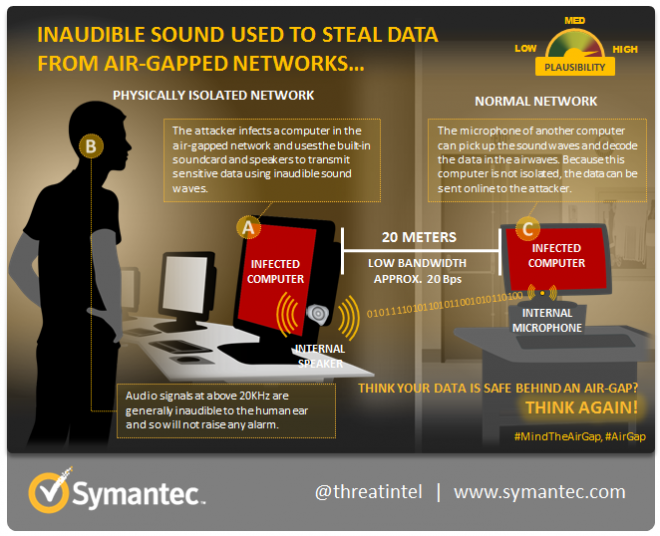
Inaudible Communication:
The data passed between two computers having no internet connection can communicate with inaudible sound. It uses built-in microphone and speakers to transfer data from the distance of 20 meters. Researchers called them Acoustical Mesh Networks, which uses sound frequency between 20 kHz to 23 kHz. The most effective method to transmit data is ACS (Adaptive Communication System) which is ideal for underwater communication.
Inaudible Communication Mitigation:
It is plausible for attackers to make attack successful due to inbuilt speakers and microphone in air-gapped network. To disable this attack, system admin persons can disable the audio output and input devices. System administrators should remove audio output hardware and use headphone instead. When in no use, a headphone should be disconnected from the system. Even the use of audio intrusion detection and audio filtering can mitigate this type of attack.
User of Scanners/Printers:
Adi Shamir (an inventor of the RSA cryptographic system), Yuval Elovici and Moti Guri from Ben-Gurion University in Israel have discovered a technique at 2014 Black Hat Europe Conference. Where an attacker sends command via printer attached with a scanner to which air-gapped system is connected.
If the source of light hit repeatedly at the white coating inside the printer attached with a scanner’s lid during the progress, an attacker can reveal the data with the outcome image that includes a white line on a dark background. Researchers developed “Morse code” (A telegraph code in which letters and numbers are presented by a thread of dots and dashes) is used to send and receive several hundreds of bits of data. The Morse code sends pulses of light periodically and understands the outcome result in binary language. Attackers need a shining light, infrared, and scan running. An attacker can send data from the distance of five kilometers. An infected computer can start scanning or wait for someone to start the scanning.
Mitigate from Air-gapped Scanners/Printers:
However, this technique requires preconditions like multi-functional printer with a scanner (connected to the air-gapped network), the scanner should be in use, an open door in the room where the air-gapped network is placed.
Conclusion:
Air-gapped system is believed to be a secure system, but the above research points out at safety awareness about such system. Cyber criminals always try hard to find a weakness in the system, so it is wise to have the above-discussed precautions. Each system is insecure, until you wish to take precaution for it.